In our previous post, we established that Private Shared State (PSS) is the solution to decades of digital conflict. We argue that it’s the answer to the crisis of trust that has long forced us to choose between massive utility and fundamental privacy. We showed that PSS could be considered a modern realization of Nick Szabo’s “God Protocol,” a system that computes correctly and confidentially on shared data.
We concluded that previous attempts at this (whether through early, non-verifiable MPC in Web2 or through siloed, non-collaborative ZK in Web3) failed due to a lack of dedicated, efficient infrastructure. This failure reflects the Digital Trilemma: the inability to achieve Decentralization, Privacy, and Verifiability simultaneously.
Our core mission at TACEO is to provide the network layer that makes PSS real. We achieve this by combining two powerful cryptographic fields in an accessible, decentralized fabric:
- Confidentiality & Decentralization (MPC): We use MPC protocols to ensure data is secret-shared across mutually distrusting nodes, providing privacy and a decentralized architecture.
- Verifiability (ZK / coSNARKs): We integrate ZK and related systems (specifically coSNARKs) to provide public verifiability. This moves beyond the “trust me, bro” problem; anyone can verify the computation was executed correctly, even though the data remains hidden.
The TACEO Network is the verifiable, accessible fabric that gives MPC and ZK the scale and interoperability they lacked. We are no longer limited by the trade-off of the Digital Trilemma.
The Foundational Architecture of the TACEO Network
Before looking into the specific services, it’s useful to recap the physical structure that hosts the Private Shared State. The TACEO Network is a dedicated, decentralized cryptographic compute network designed to coordinate secure computation and guarantee the integrity of PSS.
Inside the TACEO Network
The network operates across three main layers to manage the PSS:
- The Coordination Layer: Acts as the “traffic controller,” assigning computation jobs (like an OPRF query or an OMap update) to specific MPC node clusters, monitoring performance, and managing the cryptographic commitments to the shared state.
- The MPC Node Network: A globally distributed set of nodes that perform the Multiparty Computation. They operate in specialized committees to execute tasks securely and efficiently on encrypted data shares.
- The coSNARK Engine: The final step, where nodes jointly generate a succinct proof of correctness. This proof is verifiable by anyone, providing the same transparency guarantees as a public blockchain without revealing any private data.
Every computation on this network produces an updated, verifiable PSS commitment and a coSNARK proof.
The core visionary leap we must now make is moving past the idea of privacy as isolation (a locked vault) and turning private state into a tool of continuous, verifiable, collaborative computing.
With the core network architecture in place, we can examine the first services that make Private Shared State practically usable.
The First Essential Services for PSS
Now that we have the network in place, a pressing question emerges: what are the most critical, high-value operations we must solve to make Private Shared State functional?
The answer reveals the need for the three foundational services in this new PSS world: TACEO:OPRF, TACEO:OMap, and TACEO:Proof.
1. TACEO:OPRF - The Private Recognition Service
The most fundamental task for any application is recognition. If every piece of data in the PSS is encrypted, how does the system perform the most essential action required of any application: recognizing a user without tracking them?
- The Problem: In a privacy-first world, you need an identity mechanism that serves as a private anchor. It must verify a user’s uniqueness (anti-Sybil) to grant them access or limit an action, without linking their identity across different services or even different actions. Traditional identity systems rely on a single, permanent, and therefore trackable, identifier.
- The Solution: The Oblivious Pseudorandom Function (OPRF). This is a two-party cryptographic protocol where a client gets the output of a function on their input, using the server’s secret key, while the server learns nothing about the input or the output. In the TACEO Network, this allows the user (client) to input their unique ID and the network (server) to apply its secret key to output a third, unique value (a nullifier or pseudonym).
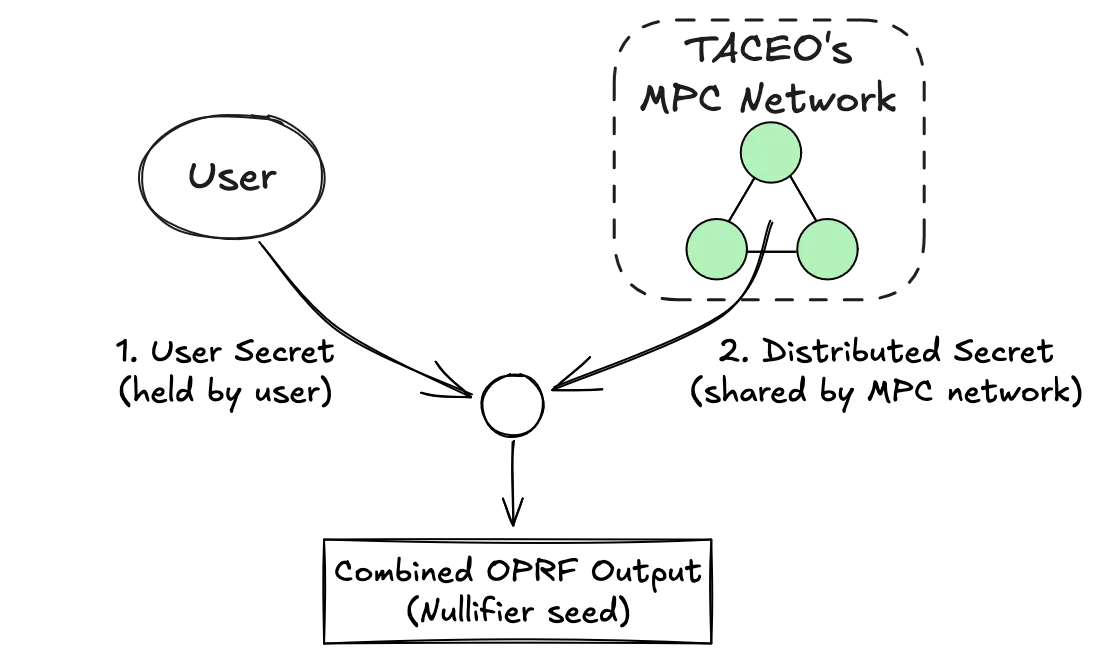
The output is unique and unforgeable, allowing a service to say: “I recognize this anonymous token has completed this action before,” without ever knowing who the user is or where else they’ve acted.
This is a deployed necessity for identity systems that need to generate a provably unique, unlinkable nullifier for every action. For instance, systems like World ID rely on this core mechanism to enforce unique personhood without compromising user privacy.
2. TACEO:OMap - The Private Lookup Service
Once the network can recognize users privately, it needs to handle the state itself. All applications ultimately revolve around a database: looking up an index, retrieving a value, and updating it.
- The Problem: The Access Pattern Attack. In a shared, encrypted state, the greatest privacy threat is the mere act of accessing a piece of data. If a server sees you query the same memory location ten times, it learns something about the data you are interested in, even if the data itself is encrypted. This access pattern leakage breaks all standard encrypted databases.
- The Solution: The Oblivious Map (OMap). An OMap, typically constructed using Oblivious RAM (ORAM), is the first data structure that can implement a “private and provable hashmap.” It allows the network to read a sender’s balance, check if an ID is registered, or verify a condition, such that every single query looks identical to an outside observer. The memory access trace is randomized and independent of the actual key being queried.
The TACEO:OMap is the operating system’s kernel for Private Shared State. It is the atomic, provable ledger layer, making it possible for applications to look up and update balances, registries, or any other shared data confidentially and verifiably. Without it, core PSS use cases (like private token transfers) are hard to achieve efficiently at scale.
3. TACEO:Proof - The Proof Delegation Service
While the TACEO:OPRF and TACEO:OMap are the primary services for private computation, the network’s third core service is responsible for its verifiability.
- The Problem: Generating Zero-Knowledge Proofs (ZKPs), especially complex ones, is often computationally expensive for end-users, especially on mobile devices or browsers. This delegates the trust of proof generation to the entity requesting the proof.
- The Solution: Private Proof Delegation.
TACEO:Proofallows an application or end-user to outsource the generation of a coSNARK proof to the decentralized, high-performance TACEO Network. The network performs the computationally intensive step, the coSNARK generation, and then provides the user with the succinct, publicly verifiable proof of correctness, without ever learning the underlying private data used to generate the proof.
This provides the ultimate verifiability service, ensuring that every action taken on the PSS, from a nullifier generation to a balance update, comes with mathematical guarantees.
From Services to Solutions
The TACEO Network binds these three necessary services into coherent, industry-ready solutions, moving the benefits of PSS from theory to real-world applications in areas like Identity and Payments.
| Layer | Component | PSS Function |
|---|---|---|
| Network | TACEO Network | Establishes the trustless, verifiable, secret-shared environment. |
| Service | TACEO:OPRF | The Identity Service: Anonymous, Unlinkable Recognition. |
| Service | TACEO:OMap | The Storage Service: Oblivious Key-Value Read/Write. |
| Service | TACEO:Proof | The Verification Service: Outsourcing ZK Proof Generation. |
| Solution | Identity Solutions | Anti-Sybil/Uniqueness checks built on TACEO:OPRF and TACEO:Proof. |
| Solution | Payment Solutions | Private Payments built on TACEO:OMap for confidential token transfers. |
The Vision of Private Payments
The Problem: How do you move funds publicly on a decentralized ledger while keeping balances and transaction amounts completely confidential?
The Solution: The convergence of TACEO:OMap and TACEO:Proof delivers the ultimate vision of a Private Payments solution.
- Secret-Shared State: User balances are stored as secret shares using the
TACEO:OMapservice. - Oblivious Computation: When a transfer occurs, the network uses
TACEO:OMapto obliviously look up the sender’s secret-shared balance and update both the sender’s and receiver’s balances. - Verifiable Integrity: The network uses
TACEO:Proofto collectively generate a coSNARK that verifies: “Yes, the sender had enough funds, and the debit/credit was mathematically correct,” without revealing the actual balances or addresses accessed.
This redefines blockchain transparency. We are moving towards private, compliant, and on-chain transactions where the data is hidden, but the integrity of the total system is publicly verifiable.
The Vision of Trustless Identity
The Problem: How do you enforce integrity (e.g., one claim per person) in decentralized identity systems without introducing a central tracking authority?
The Solution: The collaboration between TACEO:OPRF and TACEO:Proof creates the infrastructure for private digital citizenship.
- Blind Generation: A service calls
TACEO:OPRFwith a user’s scoped ID. The network blindingly generates a unique nullifier that proves the user is recognized for that specific scope. - Unlinkable Proof: The user then uses
TACEO:Proofto delegate the generation of a proof that binds the nullifier to the network’s public key. - Result: The application can check the on-chain registry for the nullifier to ensure a user is unique for that action (anti-Sybil) while being unable to link this nullifier to the user’s activity in any other scope or service. The user gains anonymity; the network gains integrity.
Performance and The “No-One-Knows” State
It’s one thing for this to be theoretically possible, but is it practical for real-world applications? The TACEO Network is specifically engineered to parallelize the most intensive cryptographic services, breaking the common misconception that advanced cryptography is too slow.
Our architecture demonstrates that the PSS model is a performant, viable alternative to current centralized and public ledger architectures:
- For Payments: Our early work on Private Payments demonstrates the system can already achieve a throughput of 200 transactions per second, including the required proof generation, on reasonable MPC hardware.
- For Identity: Our
TACEO:OPRFservice is optimized for speed, leveraging efficient hash functions and cutting-edge proof systems, with proof generation for a single nullifier query executable on a mobile device in approximately 1 second.
The future we are building transcends simple financial or identity applications. Think about the implications of having a true computational “no-one-knows” state for data: Competing companies could pool confidential market data into a PSS layer, allowing a joint AI model to optimize global supply chains without any entity ever revealing its proprietary pricing or inventory levels.
Where Were You when You First Read about PSS
This post marks the beginning of our deep dive into the three services that form the foundation of PSS and the TACEO Network’s Service Layer.
If your organization is wrestling with the Digital Trilemma, if you need to compute on data that you cannot centralize, expose, or trust any single party with, Private Shared State is the solution.
Join us as we build the next generation of privacy-preserving applications!