Welcome. Private Shared State is here to define the next era of digital collaboration, a way to compute together without compromising privacy or trust.
As this is a relatively new area, it’s worth taking a moment to tour around and become familiar with what it is. So, what do we know so far?
Intuitively, it encapsulates some semblance of privacy, on some data that’s shared and accessible, and, given that it’s state, we should be able to do something with it. At its core, this post argues that PSS is the solution to a problem that has plagued internet progress for decades.
To understand a bit more, let’s take a look at some examples where we’ve seen the need for this.
Tales from Web2
In the trad-tech world, vast amounts of potential economic and social value are left on the table because organizations cannot compute together on sensitive data. Over the years big tech players competed to collect as much data from every corner of your life as possible. But still, they couldn’t get everything. Competition, data-is-the-new-oil mantras, and later, regulation, meant that the most valuable, high-stakes data remained locked away in private silos, ultimately forcing a trade-off between massive utility and basic human trust. The simplest solution, centralizing the data, would be a major failure of trust and privacy. You just can’t ask a bank and a credit card company to dump their raw user data into one shared server with e.g., Google. It’s too dangerous, legally complex, and simply, wrong.
This led to efforts to see if there could be a way to share data, not the raw data itself, but the ability to compute on it. If it could be done in a way where no single party ever sees the inputs, but everyone can trust the output, then we could unlock that massive potential value.
This is exactly what happened in a reported collaboration between Google and Mastercard to measure the effectiveness of online advertising in driving in-store purchases. Both companies desperately wanted to learn a shared, aggregate insight (e.g., campaign ROI) from their combined, private datasets. They needed a privacy-preserving mechanism to compute on their joint, encrypted state, without either party ever seeing the other’s user data.
The problem isn’t just commercial. There’s also a major social aspect. Consider the Boston Wage Study, which aimed to analyze the gender pay gap. To conduct fair and accurate research, they needed confidential, individual-level employee salary data from numerous competing firms. Companies were, rightly, unwilling to share proprietary pay lists.
In both of these landmark cases, the teams used early forms of Multiparty Computation (MPC) protocols to conduct their statistics. But here’s the kicker: these attempts were incredibly hard to replicate. Efficiency at the time and the lack of an established, MPC network made this tech largely inaccessible. Moreover, the results were not publicly verifiable - there was still an element of “trust me, bro” in the outputs, since you had to trust the entities running the MPC.
Meanwhile, trust in big tech and government entities was declining, and the decentralized approach started to gain serious traction. People were looking for a computational layer that was not only private but provably trustworthy.
Cryptographic Ancestry & The God Protocols
If the centralized Web2 world is defined by a crisis of trust, the answer, naturally, lies in decentralization. But even here, the quest for Private Shared State is a deep, historical one.
The idea of a perfectly secure, collaborative computation protocol has been around for over twenty-five years, predating modern crypto and the invention of Bitcoin itself.
Around the turn of the millennium, cryptographer Nick Szabo wrote about what he called “God Protocols”. While Szabo first described smart contracts in 1996 (which gained life with Ethereum), his God Protocols (1999) went further. He envisioned a cryptographic engine, a distributed computation layer that would perform a task (like an auction, a contract execution, or a complex financial settlement) with perfect integrity and perfect privacy. That is, a system that acts as a trustworthy, invisible, decentralized authority.
We would much rather have a computer than God… we don’t want to pray for correct answers, nor trust in human organizations to get them, when we can have software that simply computes them correctly.” — Nick Szabo, on “God Protocols
In some way, Private Shared State is the modern realization of Nick Szabo’s God Protocol. It is the perfect blend of cryptography and distributed consensus to achieve a decentralized, private, collaborative computation.
What We’re Seeing in Web3
When Bitcoin was created, it successfully solved the core problem of shared state in a decentralized way. But to achieve this, it had to make a compromise that violated the “God Protocol” ideal: everything is public.
The inventors of decentralized ledgers knew this was a flaw.
- Satoshi’s Omission: It is widely recognized that privacy was always a needed property of distributed ledgers. Satoshi Nakamoto himself suggested that a more advanced system using a form of Zero-Knowledge (ZK) cryptography would be a superior design, but the technology simply wasn’t ready to implement at scale.
- Vitalik’s Vision: Even before the launch of Ethereum, Vitalik Buterin thought in 2014 about the potential for Secret Shared DAOs and other private applications, again, envisioning a cryptographic mechanism where the rules could be enforced on shared, yet hidden, data.
Today’s Web3 architecture, the Public Shared State of Ethereum and its counterparts, delivers verifiability and collaboration, but at the cost of a catastrophic privacy failure. Every balance, every transaction, every identity-linked interaction is a matter of public record.
The modern ZK space attempts to fix this by creating Private Isolated State. It maintains verifiability and provides privacy, but it’s fundamentally siloed. This isolation stems from the design: most ZK systems are built to allow a single Prover (an individual or entity) to prove a statement about their own private data to a public Verifier. The data remains locked inside that single prover’s domain and is never mathematically shared with or composable with data from others. This prevents the kind of large-scale, cross-organizational utility seen in the Google/Mastercard or Boston Wage Study examples, which inherently require computation over multiple independent inputs.
We’re led to an interesting conclusion: The next leap isn’t necessarily just about making data private; it’s about making private data functional and collaborative.
So, where do we stand. We’ve seen that we need decentralization. We’ve seen that we need verifiability, and that ZK is a viable route. We see that we need a way to collaborate on data, and that MPC is a viable route. Previous attempts failed due to a lack of infrastructure to support and manage the complex cryptographic operations and poor efficiency.
This is the gap we are here to close.
At TACEO, we are building the TACEO Network, the decentralized cryptographic compute fabric that establishes and governs this PSS model.
From Concept to Network
Private Shared State needs an environment to live in. It needs an infrastructure that can coordinate computation, preserve confidentiality, and still provide public verifiability.
That is what we’re building with the TACEO Network.
It combines two foundational technologies, Multiparty Computation (MPC) and collaborative SNARKs (coSNARKs), to make collaborative computation over encrypted data both practical and verifiable.
Inside the TACEO Network
Under the hood, the network consists of three main layers:
-
The Cryptographic Coordination Layer:
Acts as the “traffic controller,” assigning computation jobs to node clusters, monitoring performance, and managing state commitments.
It ensures that no single participant can dominate the computation or manipulate outcomes.
-
The MPC Node Network:
A globally distributed set of nodes that perform the actual multiparty computation.
They operate in committees to execute tasks securely and efficiently, scaling to different performance or trust requirements.
-
The coSNARK Engine:
Once computation is complete, these nodes jointly generate a proof of correctness.
This proof is succinct enough to be verified directly on any chain or by any participant — providing the same transparency guarantees that blockchains pioneered, but without the privacy cost.
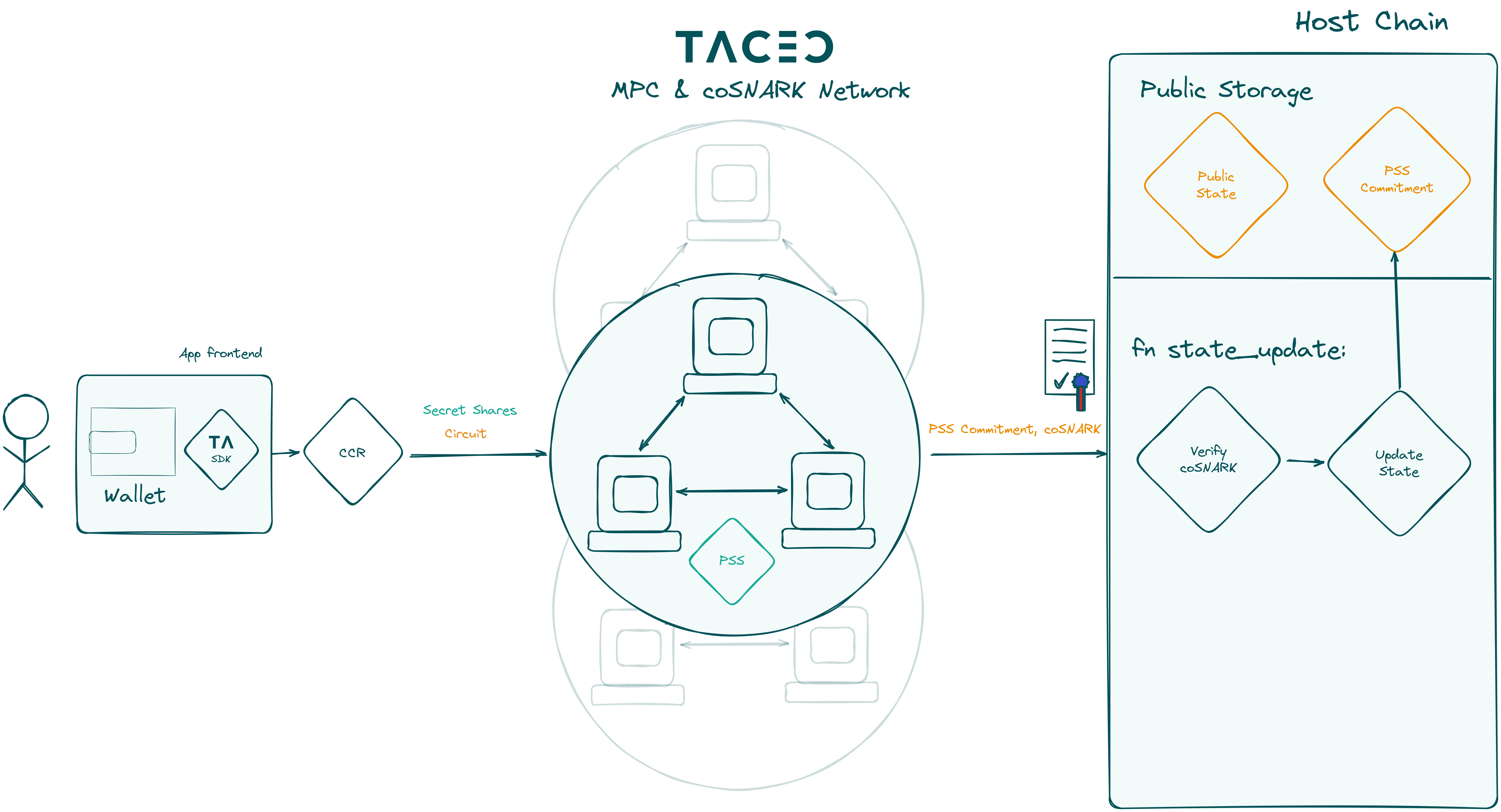
Every computation on the TACEO Network produces two outputs:
- A PSS commitment, which encodes the updated encrypted state.
- A coSNARK proof, which guarantees that this update followed the agreed rules.
Both can then be verified by smart contracts or external systems, bridging private computation and public accountability.
How It Works
At a high level, here’s what happens when someone uses the TACEO Network:
-
Inputs are encrypted and shared among a committee of independent compute nodes.
No single node ever sees the full input and each holds only a mathematical fragment.
-
Computation happens collaboratively through a secure MPC protocol.
The nodes jointly compute the requested function (e.g., a credit score, a vote tally, or a transaction match) directly on the encrypted fragments.
-
A succinct proof (coSNARK) is generated to attest that the computation was done correctly.
Anyone can verify the result (on or off-chain) without rerunning the computation or accessing private data.
-
The output is published as an updated private shared state, optionally settled on a host chain.
These steps can be traced on the graphic above. This streamlined process delivers a verifiable, updated Private Shared State ready for developers to build upon.
Programmable Cryptography
We believe in the promise of programmable cryptography, and built the network to support this.
We believe that developers shouldn’t have to understand multiparty protocols or zero-knowledge proving systems to work with Private Shared State.
Through TACEO’s DSL extensions (like coCircom and coNoir), developers can define functions that automatically compile into secure MPC + coSNARK workflows.
In other words, you write the logic and the network handles the cryptography.
This makes it possible to create verifiable, privacy-preserving smart contracts that live across both private and public chains.
What Becomes Possible
When encrypted collaboration becomes trustless, a new class of applications opens up:
- Private identity and credit systems – compute scores or verify credentials across institutions without exposing user data.
- Dark pools and confidential trading – match large orders privately while ensuring provable fairness.
- Collaborative governance – conduct encrypted votes that are both secret and publicly verifiable.
- Verifiable machine learning – privately train or evaluate models on distributed private datasets with cryptographic proof of correctness.
- Private social networks – privately compute collective trust or reputation scores from encrypted inputs.
All of these rely on the same underlying idea: multiple entities computing on shared, encrypted state that only the TACEO Network itself ever “sees.”
A New Foundation for Decentralized Computing
It has been clear for a long time that there is a need for verifiable encrypted compute. Since the 80’s, academia has been working towards proving without revealing (via ZK) and computing on encrypted data (via MPC). It’s only in the past couple of years that the technology has become viable for real world use. The ideas are there, the tech is ready, now the TACEO Network exists to deliver the infrastructure that allows to retire the compromises of the old internet.
Where existing systems offer transparency, TACEO brings confidentiality.
Where trust in off-chain actors was needed, TACEO offers proofs.
And where private computation was once siloed, TACEO makes it shared.
Together, these form the backbone of Private Shared State, the next paradigm in verifiable decentralized computing.
In the next post, we’ll explore how this foundation is extended through TACEO:Proof, TACEO:OPRF, and TACEO:OMap. These are the first services on the TACEO Network that make Private Shared State practical for developers and enterprises. Follow TACEO on X for the latest news.
