Today, the TACEO:OPRF Public Beta goes live on the TACEO Network.
If you’re building identity systems, credential infrastructure, or anything that needs privacy-preserving nullifiers without single points of failure: this is your starting point. Eight independent node operators. Verifiable computation.
test.oprf.taceo.network is open. (> TACEO:OPRF Docs)
For the full technical context on why we built this, read our Introducing TACEO:OPRF deep dive. What follows is what’s new, and how to start building!
What’s Live Today
What you get:
- Threshold architecture
- Verifiable computation: cryptographic proofs that the OPRF was computed correctly
- Fast core latency: ~130ms OPRF computation without proof generation; ~1-3 seconds end-to-end including ZK proofs (depending on the authenticator and client side proof system)
- No single point of failure: compromising a node reveals nothing
- Free tier access at
test.oprf.taceo.networkfor developers and researchers
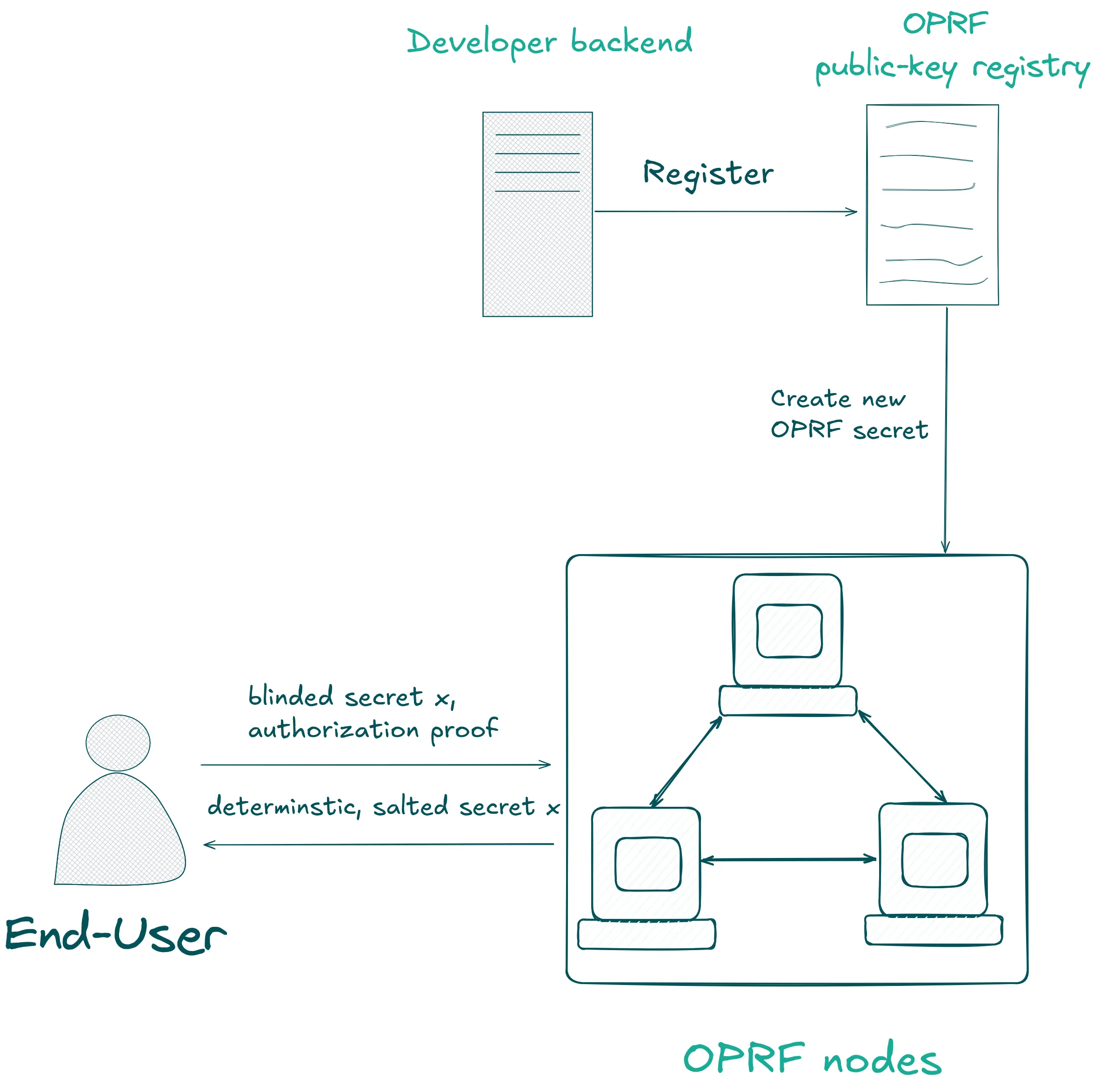
No single operator sees the full secret. No single operator can link nullifiers. This is distributed trust in practice, a live network you can query today.
Use Cases: Where Privacy Needs Resilience
The threshold OPRF is a foundational primitive. Its core insight is simple: what if no single party, not even the user, held the complete secret? Instead of one secret key, the cryptographic operation is distributed across independent parties. Each holds a share. No single party can reconstruct the full key or link outputs together.
Here’s where that matters most.
Privacy-Preserving Identity
Zero-knowledge identity systems like Semaphore, Polygon ID, and others use nullifiers to prevent the same person from claiming benefits, voting, or accessing a service multiple times, without revealing who they are. Traditionally, these nullifiers are derived from a single user-held secret key.
The Problem: If that secret ever leaks, through a compromised device, social engineering, or user error, it doesn’t just compromise one action. An attacker can recompute every nullifier that user ever generated, across every service, every interaction, retroactively. For systems processing millions of users, this isn’t theoretical. It’s an operational certainty.
The Solution: With threshold OPRF, the nullifier is generated collaboratively across multiple independent parties. The user’s secret alone is insufficient to reconstruct past nullifiers. Even if the user’s key is compromised, an attacker would also need to break the MPC threshold assumption, corrupting a majority of independent node operators, to trace a single user.
Each identity verification remains unlinkable. Privacy becomes persistent, not fragile.
This is the architecture powering real deployments today. The first production integrations are already live, with major announcements coming soon.
Builder Codes: Privacy-Preserving Revenue Sharing
Wallets like MetaMask, Trust Wallet, and Ledger route millions of transactions to AMMs and blockchain platforms every day. This orderflow has real economic value, and platforms want to compete for it through revenue-sharing arrangements.
But there’s a tension: on public blockchains, attributing orders to a wallet means exposing your user base, your volume, and your routing strategy to every competitor watching on-chain. Wallets want to get paid for the orderflow they generate. They don’t want to reveal their business in the process.
Builder Codes solve this. Using OPRF, wallets generate a private, verifiable tag proving they originated a given set of transactions, enabling revenue-sharing without revealing which user sent which order, and without exposing aggregate volume or routing patterns. Attribution without exposure.
We’re publishing a companion deep dive on Builder Codes shortly.
Provably Unique Access Control
One anonymous access per person, for voting, airdrops, ticket sales, or governance, without tracking who accessed what. Generate a nullifier to mark a slot as used. The system enforces uniqueness. Nobody learns who you are or links your actions across different systems.
To make this concrete, we built a voting demo that puts three privacy models side-by-side: OPRF Voting Demo
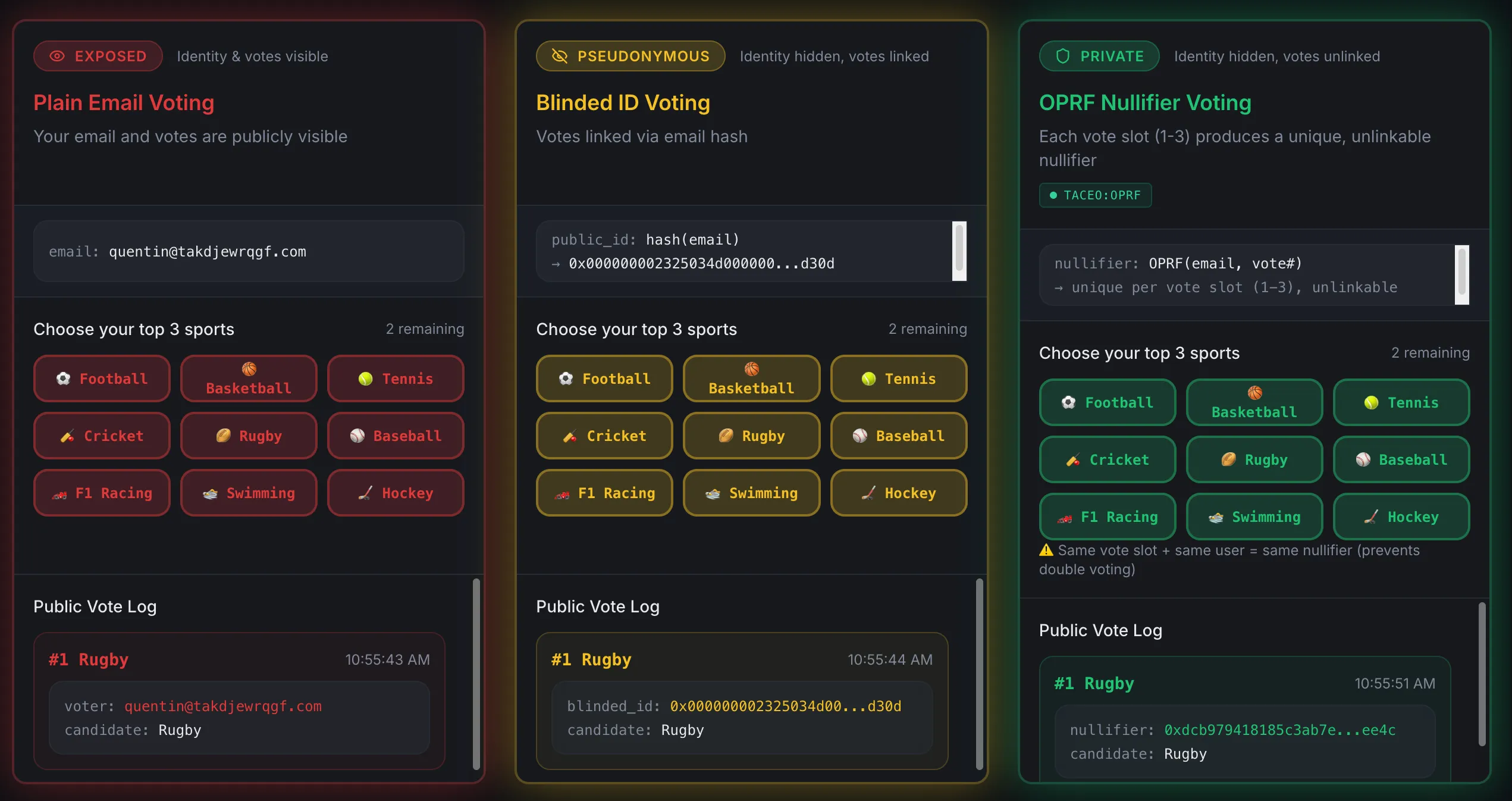
Cast the same votes three times, and watch what each model reveals:
- No privacy: Your email and choices are fully visible. Anyone can see who voted for what.
- Hashed identity: Your email is replaced by a hash, but every vote you cast is still linkable to the same pseudonym. An observer can reconstruct your full voting pattern.
- OPRF nullifiers: Each vote gets its own unique, unlinkable nullifier generated via threshold OPRF. Nobody, not even the server, can connect your votes to you or to each other.
How It Works
The OPRF protocol, simplified:
- Blind the input: You have some identifier (biometric hash, credential, secret). You cryptographically mask it so nodes can’t see what you’re computing.
- Distributed computation: Each node applies its share of the secret key to your blinded input.
- Threshold reconstruction: The client combines responses from a threshold of nodes (e.g., 5 of 8).
- Unblind the output: Remove the mask to get your final nullifier. Deterministic, unique, unlinkable.
- Verification: A cryptographic proof confirms the computation was performed correctly.
Key property: No single node sees your input. No single node can link outputs. Compromising any subset below the threshold reveals nothing.
Verifiable computation is what separates this from trust assumptions. Every OPRF computation includes a zero-knowledge proof that the nodes performed the calculation correctly. Even if malicious nodes try to compute the wrong output, the verification proof will fail. The system rejects bad computations automatically. Don’t trust us, verify.
Performance: A single OPRF invocation takes ~130ms for the core computation and ~1-3 seconds end-to-end including ZK proof generation and verification (depending on the authenticator and client side proof system). The proof computation (using Barretenberg in this Beta), is the most expensive step.
Try It Today!
- Endpoint:
test.oprf.taceo.network- Access: Rate-limited, public API.
- Use case: Prototyping, research, learning
- Get started:
- Check the developer docs
- Clone our GitHub repo
- Run your first OPRF computation in under 5 minutes
- Ready for production? For identity systems, DeFi infrastructure, and credential platforms, we offer dedicated environments with custom SLAs, higher throughput, dedicated node configurations, and integration support from our cryptography team.
- Contact us
What’s Next
OPRF is the first service running on the TACEO Network, but it’s not the last.
We’re building an Encrypted Compute Layer, a stack of privacy-preserving services, each solving a different hard problem in confidential state management.
Coming soon: TACEO:OMap, the “Private Lookup Service”, enabling verifiable storage and retrieval of confidential shared state, essential for private ledgers and registries (Read more: Introducing TACEO:OMap).
The network is live. The first threshold OPRF service is open.
What will you build with it?
Get Involved
Try the Beta: TACEO:OPRF Beta repo
Read the docs: docs.taceo.io
Acknowledgments
The TACEO:OPRF Service wouldn’t exist without our partners, who believe privacy is infrastructure, not a feature.
And to the builders experimenting with and integrating OPRF: thank you for the trust, the feedback, and the vision of what privacy-preserving systems can become.
Recognition without exposure. Privacy without single points of failure. Welcome to TACEO:OPRF Public Beta.
