The crypto industry, long been associated with pseudonymity and user sovereignty, starts to face the rising tide of global regulatory enforcement. From the EU’s MiCA and AML Authority to US Treasury rules and the FATF Travel Rule, AML and CFT requirements are tightening, and now reaching into DeFi and protocol-layer systems. This introduces a fundamental paradox: how can an industry built on principles of decentralisation and privacy reconcile itself with the demands of KYC, particularly around identity verification, data retention, and regulator access?
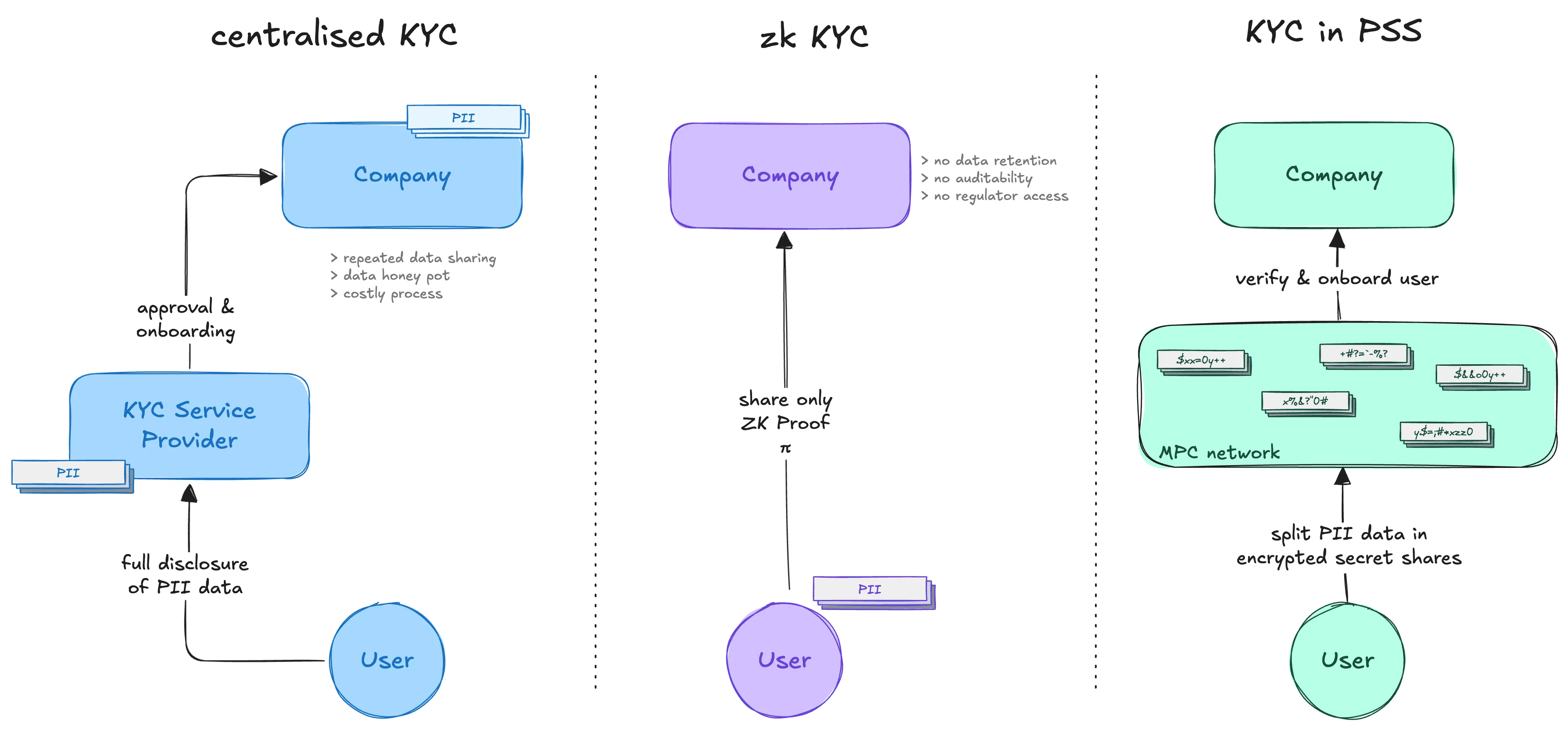
The status quo relies on centralised KYC systems, which pose several problems. Users must repeatedly submit sensitive identity data to each platform, resulting in data duplication and fragmented user experience. These silos create high-value targets for attackers, with multiple well-documented breaches and enforcement actions revealing the systemic risks. The privacy implications are equally profound, as companies are often forced to store personally identifiable information despite not being data-centric businesses.
We argue that new architecture is needed, one that satisfies regulatory requirements without compromising user privacy.
More granular tools, but deeper needs
Zero-knowledge proofs provide a powerful cryptographic mechanism for selective disclosure. They allow users to prove that certain statements are true, like being over 18 or not appearing on a sanctions list, without revealing the underlying data. This makes ZK ideal for ephemeral or attribute-based use cases and has seen the emergence of privacy-preserving credential systems in decentralised identity.
Yet, full KYC compliance introduces broader demands. Regulatory frameworks in the EU and US require that identity data be retained, made available to authorities upon request, and subject to audit over time. These obligations cannot be met by ZK-only systems, which assume a single prover and do not accommodate persistent, collaborative data handling. Client-side zero-knowledge identity wallets give users control, but they lack mechanisms for legal data recovery, continuity, or compliance-grade logging.
We propose a cryptographic architecture that supports selective access under predefined conditions, rather than a model where user data disappears from institutional reach.
A shift in the landscape
We aim for a shift in how identity is verified and stored, moving from ZK-only systems toward collaborative cryptographic infrastructure based on multiparty computation. We expect and welcome policy discussions that will enable this evolution.
Multiparty computation enables multiple independent entities to jointly perform computations on encrypted data, without any party seeing the full input. In the context of KYC, this could allow distributed nodes to execute sanctions screening, identity validation, and other AML checks while maintaining strong data confidentiality guarantees. Paired with verifiable cryptographic proofs, the result is a tamper-evident attestation of regulatory compliance.
Such a system could also support lawful data access under specific governance mechanisms. Viewing keys, threshold-based decryption, and warrant-based disclosure protocols offer a way to meet regulator expectations while minimising unnecessary data exposure.
Our goal is not to reject KYC, nor to surrender to traditional surveillance infrastructure, but rather to offer a third path where identity can be verified, user privacy can be protected, and regulation can be enforced in a decentralised, accountable, and technically sound way.
The problem with centralised KYC
The current approach to KYC is structurally flawed. Users are routinely required to submit the same Personally Identifiable Information across multiple platforms, resulting mass-duplication of sensitive data. This type of fragmented storage model creates isolated silos, each representing a potential point of failure. As high-profile data breaches and regulatory penalties have shown, the security and liability risks inherent to this model are substantial.
Beyond these risks, the process itself is inefficient. Identity verification imposes significant operational overhead on service providers and degrades the user experience through redundant onboarding processes. Even businesses that do not rely on user data as part of their economic model are compelled to collect, process, and retain it to meet AML obligations, often in tension with evolving data protection frameworks such as the GDPR.
Efforts to move beyond centralised KYC have increasingly turned to zero-knowledge proofs, which offer compelling benefits for selective disclosure. ZK allows for minimal revelation of data, for example, proving one is over 18 without disclosing a birthdate. However, while useful for point-in-time verifications, ZK alone is insufficient for comprehensive compliance. Most implementations assume a single proving party and lack the infrastructure for collaborative validation, persistent identity state, or post-hoc regulator access.
A fundamental requirement of regulated identity systems is the ability to retain and disclose information under lawful conditions. Systems designed solely around data minimisation and client-side control are not equipped to meet audit, recovery, or legal disclosure requirements. This points to the need for a more capable and decentralised architectural model that supports granular access control and verifiability without defaulting to central storage.
Introducing Multiparty Computation (MPC) and Private Shared State (PSS)
A more resilient and privacy-preserving approach to identity management could start with the combined use of MPC and PSS.
MPC is a cryptographic technique that enables multiple independent parties to compute a function jointly over their private inputs, without any party revealing its own data. In effect, it allows for collaborative computation over encrypted or secret-shared information. PSS extends this paradigm to data management: it refers to a distributed system in which multiple entities co-maintain a shared state that remains private, auditable, and tamper-evident, while ensuring that no single participant retains unilateral access or control.
We argue that MPC and PSS could form the basis for a distributed compliance infrastructure that supports both verifiable data processing and strong confidentiality guarantees. In the context of identity systems, this would allow for collaborative verification of user data without requiring centralised storage or unilateral trust. For example, the TACEO Network applies MPC for confidential execution and pairs it with coSNARKs to generate succinct cryptographic proofs of correctness, ensuring that results can be verified without disclosing underlying inputs.
MPC 4 KYC
When applied to KYC, MPC offers a structurally different model from existing approaches. Rather than transmitting and storing raw identity data on central servers, user-submitted information can be encrypted and secret-shared at the edge, then distributed across a network of MPC nodes. This means that no single entity ever has access to the complete dataset. Sensitive operations like identity document validation, politically exposed person screening, and sanctions list matching are performed jointly across these nodes using secure computation protocols.
The output of such a process is a cryptographic attestation of compliance rather than raw user data. For example, the system could issue a verifiable claim that a user has passed Level 2 KYC checks or that they do not appear on any relevant sanctions lists. These attestations can then be presented to other services without the need to resubmit or reverify identity data, significantly reducing exposure, and friction.
Moreover, the architecture could also accommodate regulator access in a controlled and auditable manner. Mechanisms for user-governed viewing keys, threshold-authorised data release, and legally constrained warrant-based disclosures can be implemented to satisfy legal obligations without undermining the system’s privacy guarantees.
This approach reworks the compliance surface of crypto infrastructure. Replacing ‘secure silos’ with a collaborative, distributed, and provably private system for identity verification, it meets the operational needs of platforms and the legal standards of regulators.
How an MPKYC System Could Work
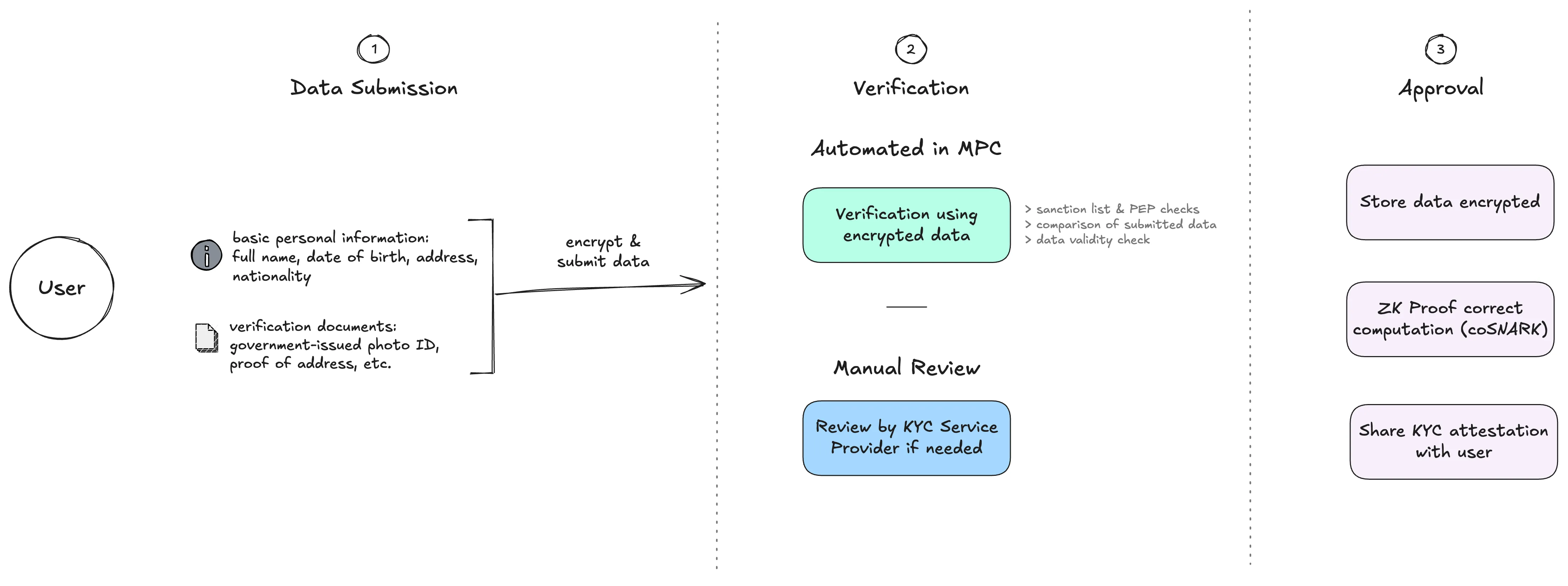
An MPC-based KYC (MPKYC) system re-architects the identity verification workflow:
- One-time KYC submission: Users submit their identity data, such as a government-issued ID and a selfie, once. This data is encrypted at the edge and secret-shared across a distributed network of MPC nodes. No single party has access to the full, unencrypted dataset.
- Distributed identity verification: All automated verification steps, such as comparing extracted passport data with user-submitted information, checking the structural validity of identity documents, or screening against sanctions lists, could be executed collaboratively over encrypted data using MPC protocols. In cases where automated checks are insufficient or inconclusive, and a manual review is required, the relevant subset of data would need to be selectively disclosed to the designated KYC provider for further examination.
- Verifiable output: Upon successful verification, the system produces a cryptographic attestation or proof indicating that the user has satisfied the required compliance checks. Simultaneously, it establishes a persistent, encrypted identity state within the Private Shared State layer. This state can be referenced by other services without the need to resubmit underlying documentation.
- Using verifiable output: When a user seeks to access a service that requires KYC, they present their attestation. The service queries the MPKYC network or PSS layer, which verifies the attestation’s validity without exposing the underlying personal data.
The system could also support a variety of mechanisms for lawful and controlled data disclosure:
- User-controlled disclosure: The user may authorise access to specific parts of their data on a case-by-case basis.
- Threshold-based disclosure: A predefined group of independent parties must jointly authorise access to encrypted records.
- Warrant-based disclosure: Data access can be triggered only through the presentation of a valid, verifiable legal warrant.
- Time-limited access: Temporary access windows can be granted for specific investigations or audits, after which access is automatically revoked.
All disclosures could be cryptographically auditable, ensuring transparency and accountability, and are strictly limited in scope, preserving user privacy while fulfilling regulatory obligations.
From the User’s Perspective:
The user’s journey is streamlined and privacy-centric:
- The user initiates the KYC process, submitting their ID and selfie from their device.
- This data is encrypted and secret-shared at the edge.
- MPC Nodes receive the encrypted shares and run the verification logic.
- A coSNARK generates a verifiable proof of correct computation, alongside an encrypted PSS commitment.
- The user receives their KYC attestation, which apps can then query to verify their status.
From the Service’s Perspective:
Services gain efficient and verifiable access to compliance status:
- An app, exchange, or protocol requests proof of KYC from the user or directly queries the MPKYC network.
- The user’s wallet or identity plugin signs the request and provides a reference to their KYC attestation.
- The MPKYC network or PSS layer verifies the attestation’s validity via the coSNARK and potentially an on-chain commitment.
- The service receives a high-level, provable status (e.g., “KYC Level 2,” “Not on sanctions list,” “Over 18”) without ever seeing the raw PII.
- Based on the verified status, the user is granted access.
- If deeper checks are required under a valid legal premise, the viewing key logic or warrant-based request mechanism is triggered, ensuring auditable and controlled disclosure.
Benefits of MPC-based KYC Networks
The advantages of an MPC-based KYC architecture could be many, benefiting multiple stakeholders:
- For Users: Significantly reduced risk of data leaks, enhanced privacy by default, and a dramatically improved user experience due to the elimination of repeated re-verification across platforms.
- For Companies: Reduced liability associated with storing sensitive PII, lower operational costs related to KYC processing, and demonstrably provable regulatory coverage.
- For Regulators: Enhanced audit trails, provable compliance from the underlying cryptographic guarantees, and a reduced risk of non-compliance stemming from data breaches or inadequate privacy safeguards.
- For the Ecosystem: A path toward robust, decentralised compliance infrastructure, bringing compliant growth to DeFi protocols, dapps, and Web3 generally.
Private stablecoins and the role of MPC-based KYC
Private stablecoins are one of the fastest growing areas within the broader crypto economy. Their appeal lies in the promise of fast, low-cost, and censorship-resistant digital payments, while maintaining a stable value that can be used for real-world economic activity. However, as adoption extends to more sensitive domains such as payroll, business-to-business settlements, and financial contracts, existing public-chain infrastructure presents a critical limitation.
Every transaction on a public blockchain is, by default, transparent. Sender and recipient addresses, transaction amounts, and token types are permanently visible. While this transparency may serve public accountability in some contexts, it is not compatible with the privacy requirements of commercial activity. Few companies are willing to expose their supplier relationships, employee compensation, or internal cash flows on a public ledger.
To address this, privacy-preserving stablecoin protocols are beginning to emerge. These solutions typically use zero-knowledge proofs and other privacy-enhancing technologies to obscure one or more transaction attributes. Depending on the implementation, it may be possible to hide the sender, the recipient, the transaction amount, the token itself, or some combination of these. We’re starting to see designs also incorporating viewing keys that allow designated entities, such as auditors or compliance officers, to decrypt transaction details under specific conditions.
However, decrypting a transaction with a viewing key may reveal which wallets interacted, but it still does not reveal who the individuals or entities behind those wallets are. In other words, the system still does not know the customer. From a compliance perspective, there is a gap. Regulators and payment counterparties require not only transactional transparency when warranted, but also the ability to associate those transactions with verified identity information.
A solution to this challenge could be the integration of MPC-based KYC (MPKYC) into the design of private stablecoin systems. By linking private transaction activity to the encrypted identity attestations generated through MPC, a stablecoin network could achieve both strong privacy and regulatory compliance. Instead of revealing full identity details with each transaction, the system could attest that both the sender and recipient have passed required KYC checks, are not on sanctions lists, or meet other criteria, without disclosing their identities to each other or to the public.
Such attestations could be cryptographically verifiable, reusable, and subject to policy-based access when deeper inspection is necessary. This approach does not rely on trust in any single party and avoids placing identity data in centralised databases. Instead, identity and compliance checks would be distributed, auditable, and aligned with the privacy expectations of both users and institutions.
If private stablecoins are to become viable at scale, particularly in institutional or cross-border use cases, integrating a secure, decentralised, and privacy-preserving KYC layer may be essential. MPKYC offers a path toward achieving this, serving as a foundational building block for the next generation of privacy-respecting digital payment infrastructure.
Challenges and the way forward
While the potential of MPC for KYC is significant, several open challenges remain. One of the most pressing is the need to define legal responsibility for the “obliged entity” in a decentralised, multiparty system. Regulatory frameworks are typically built around identifiable institutions, and adapting them to distributed architectures will require careful legal interpretation and possibly new policy constructs. Similarly, mechanisms for controlled data access, such as threshold-based or warrant-triggered disclosures, must be designed with strong technical guarantees and subjected to legal scrutiny to ensure they meet compliance standards.
Widespread adoption will depend not only on technical feasibility but also on regulatory engagement. This includes participation in sandbox environments, the generation of verifiable reliability proofs, and close alignment with international legal requirements. On the technical side, MPC and coSNARKs introduce non-trivial computational costs. Real-world deployment will require continued work on optimisation, protocol design, and infrastructure scalability.
It is important to recognise that zero-knowledge tools, while valuable for selective and ephemeral disclosures, are not sufficient on their own to support the full spectrum of compliance requirements. In contrast, MPC integrated with Private Shared State could offer a comprehensive and balanced architecture.
The tension between privacy and regulation in the digital asset ecosystem is not inherently irreconcilable. We believe that MPC-based KYC presents a credible path forward. It can offer a way to satisfy legal obligations without reverting to centralised data collection, enabling identity verification that is both privacy-preserving and regulator-compatible. Rather than a compromise of principles, this represents a practical shift toward aligning cryptographic integrity, individual privacy, and institutional responsibility.
We believe MPC-based KYC represents a viable path toward reconciling privacy and regulation in Web3. If you’re building identity infrastructure, stablecoins, or compliance tooling, or if you’re a regulator curious about cryptographic enforcement, we’d love to collaborate. Reach out on X to explore the TACEO project to get involved. You can also subscribe to our newsletter or chat with us in Discord!
Many thanks to Arnaud Schenk for conversations on the topic, and comments on this post.
